Page 10 - AeM_September_2020
P. 10
RESEARCH
ANALYSIS
TRENDS
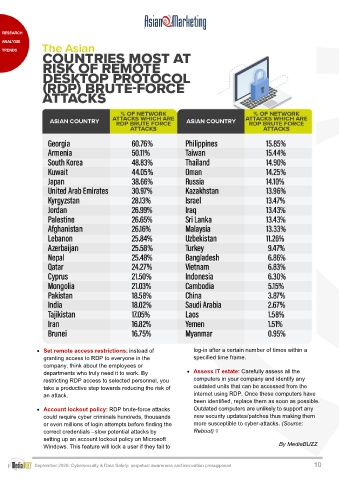
• Set remote access restrictions: instead of log-in after a certain number of times within a
granting access to RDP to everyone in the specified time frame.
company, think about the employees or
departments who truly need it to work. By • Assess IT estate: Carefully assess all the
restricting RDP access to selected personnel, you computers in your company and identify any
take a productive step towards reducing the risk of outdated units that can be accessed from the
an attack. internet using RDP. Once these computers have
been identified, replace them as soon as possible.
• Account lockout policy: RDP brute-force attacks Outdated computers are unlikely to support any
could require cyber criminals hundreds, thousands new security updates/patches thus making them
or even millions of login attempts before finding the more susceptible to cyber-attacks. (Source:
correct credentials –slow potential attacks by Reboot) ◊
setting up an account lockout policy on Microsoft
Windows. This feature will lock a user if they fail to By MediaBUZZ
September 2020: Cybersecurity & Data Safety: perpetual awareness and innovation presupposed 10